Accessing the Private Virtual Network
Accessing the Private Virtual NetworkAccessing the private virtual network is no different to access any lab network through a gate way system
1. Accessing internal Web Servers with an Apache Reverse Proxy Server Configuration
The global zone can be configured to run an Apache web server as reverse proxy. This allows to direct a browser to web port of the global zone public network interface and work with a specific web server of the internal private virtual network.
The following example assumes that zone1 offers a http service through port 80 at the internal IP address 192.168.0.2.
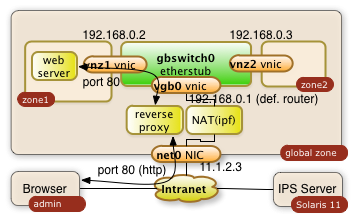
It will be made available to 11.1.2.3
1.1. Configure configuration file of Apache 2.2 in global zone
The proxy server gets configured through the httpd.conf file with the following directives:
/etc/apache2/2.2/httpd.conf:
|
... ServerName myglobalZone.public.name.com ... ProxyRequests Off ProxyPass / http://192.168.0.2/ ProxyPassReverse / http://192.168.0.2/ ... |
The three directives avoid that the Apache server acts as a regular proxy (ProxyRequests Off). The ProxyPass and ProxyPassReverse directives teach the server to relay all http requests ( / ) to 192.168.0.2/ and the responses back. The ending slashes matter!
1.2. Start the Apache Server in the global zone
Start or restart the server with the following priviledged Solaris command in the global zone:
$ svcadm restart svc:/network/http:apache22
The svcadm command starts the Apache server on Solaris as a service. This command assures that the service is up even after a reboot of the system. This is all it takes on the proxy side!
This setup of the reverse proxy does the job for pretty much every simple web server behind it.
Warning: The web server in the private network may have to know that it's http service is getting exposed by a reverse proxy. Some web applications generate URLs on the fly. This post configuration is however completly application specific
2. ssh Tunnels
A more ad-hoc and very safe way to access a port in your private virtual network is a ssh tunnel.
The user on system admin will need an account in the global zone of the Solaris 11 system (IP address: 11.1.2.3). The account name being used in this example is guest.
ssh tunnels allow to plumb a port of a remote system to your local system. The following command will plumb the port 80 of zone1 to port 7777 of the desktop the user admin is using:
$ ssh -L 7777:192.168.0.2:80 guest@11.1.2.3
The command will lead to a shell session of user guest in the global zone. Besides this you will get the tunnel to be established. The user on system admin can now direct a browser to http://localhost:7777 a use the web server from zone1. The diagram below shows the interactions of the three systems.
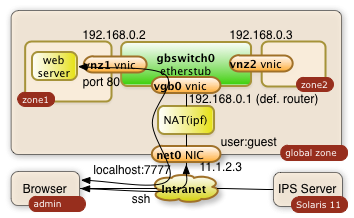
The -L can be used multiple times in a single command. It'll tunnel any number of ports needed.
References
- 4045 views